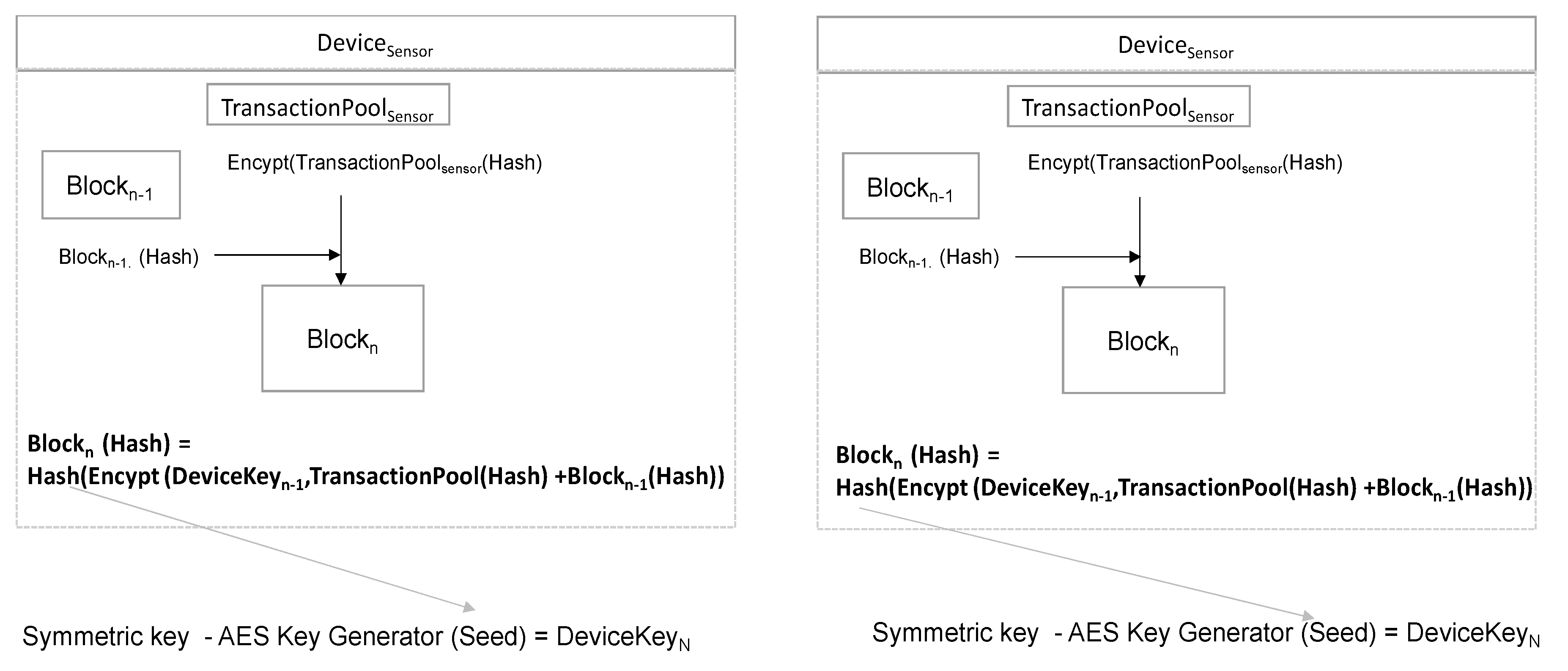
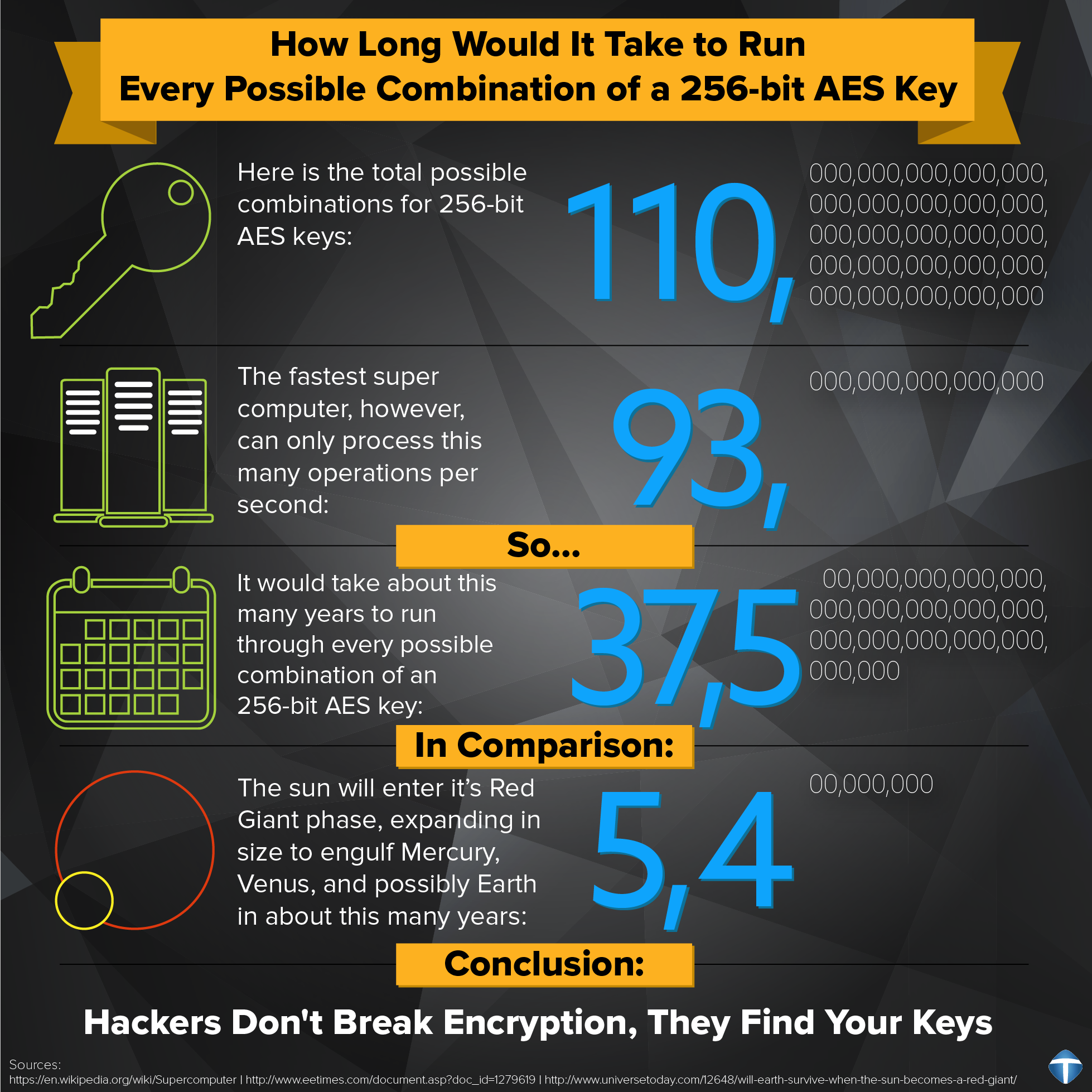
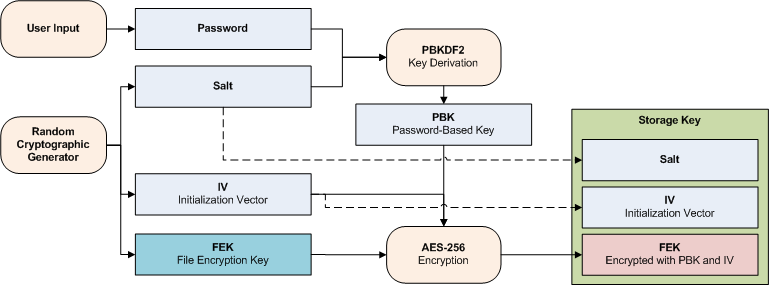
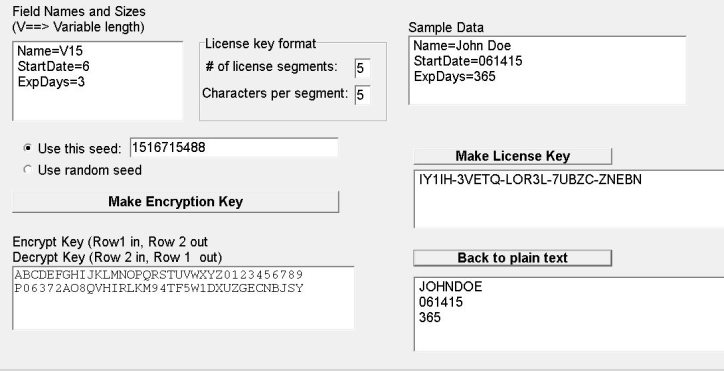
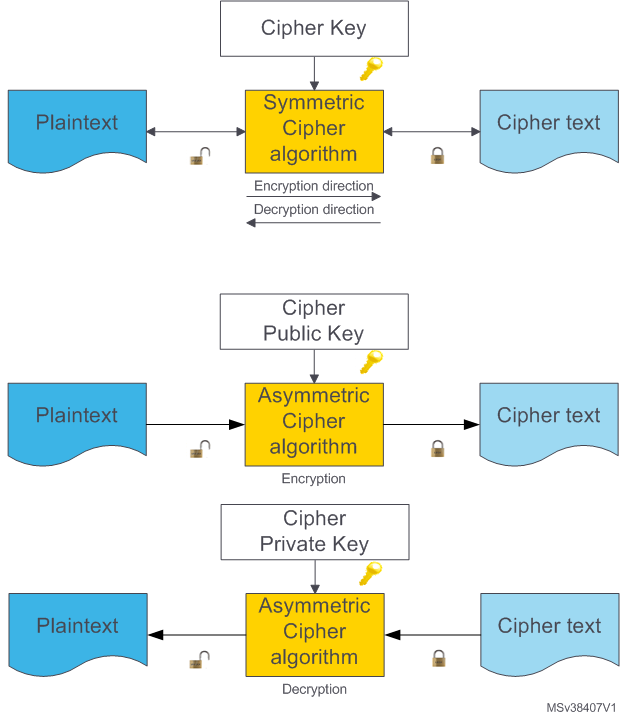
Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen

CJMCU 608 Cryptographic Key Storage Random Number Generator Signature Encryption Decryption Module|encryption keys| - AliExpress

RE-ENCRYPTION KEY GENERATOR, RE-ENCRYPTION APPARATUS, AND PROGRAM - diagram, schematic, and image 09
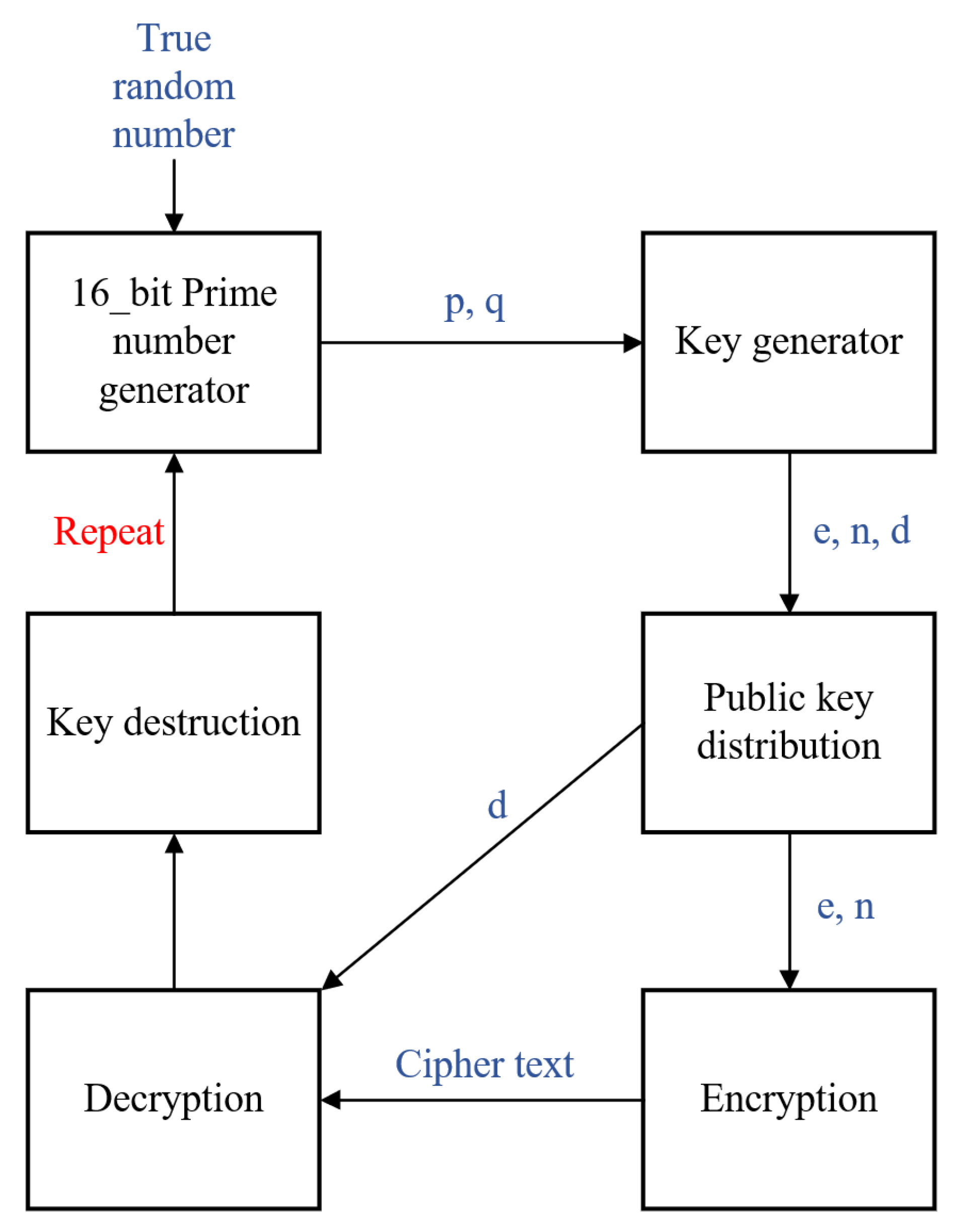
Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices
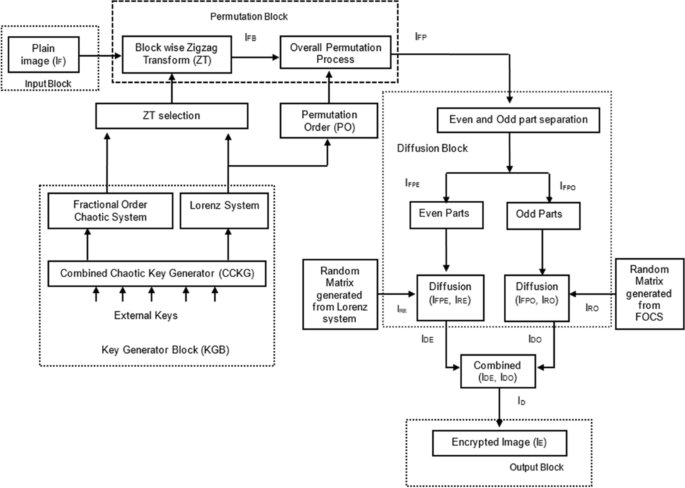
A one-round medical image encryption algorithm based on a combined chaotic key generator | SpringerLink